Policy management
There are two kinds of policy that can be configured in Antimatter. Context policy governs what happens to the data when it is written or read, and domain policy governs who can edit policy, encryption and other settings inside Antimatter.
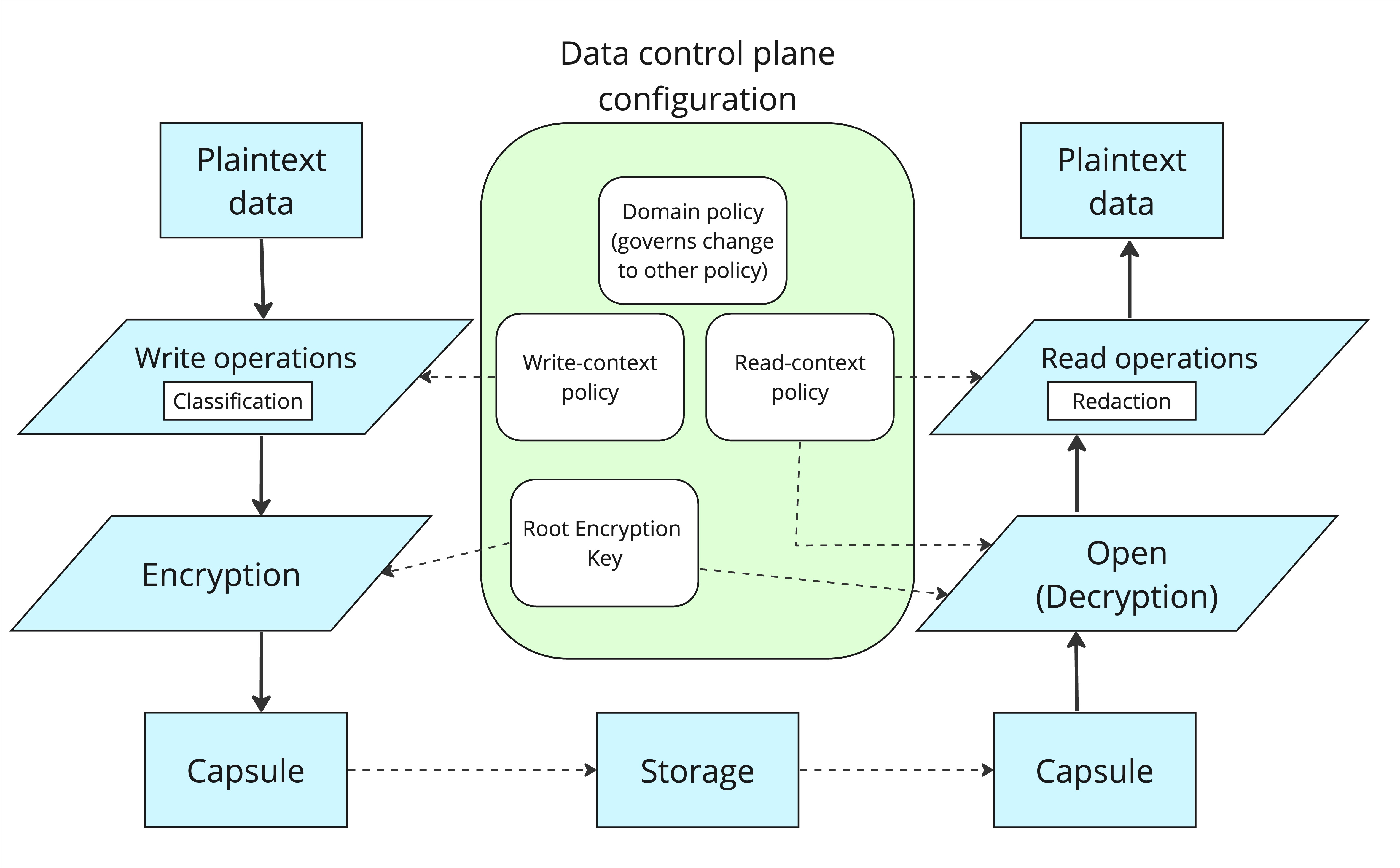
When data is first written, the write-context policy determines which (if any) classifiers are run on the data. See Write-Context Policy for more information about configuring write contexts and which classifiers are available.
Then when data is later read, it is the read-context policy that determines if the data will be permitted to be decrypted, and what transformations will apply to the data as it is read. See Read-Context Policy for more information about configuring read contexts and what kind of data transformations are available.
The domain policy rules impact what parties authenticated with Antimatter are permitted to do based upon their capabilities (similar to roles in other systems). This policy governs:
- Which read-contexts or write-contexts a user is permitted to Use.
- Which configuration (including context policies) a user is permitted to Edit or View.
See Domain Policy for more information about configuring domain policy rules. In
Imported policy
Antimatter is engineered from the ground up to support federation. This is very visible in the way policy is handled: read and write contexts can be imported from other domains, and domain policy rules can also be imported from other domains with configurable precedence. This permits you to avoid repeated configuration when using domains to compartmentalize data (e.g. for tenant isolation in a multi-tenant application), as well as allowing data owners to control data in the hands of a third party. See the respective context and domain policy sections for more information about importing and exporting policy.